ZenCash: Blockchain Decentralization as a Social Movement
May 19, 2018, 4:40pm
ZenCash is a fork of ZCash that aims to be a catalyst for social change and collaboration across a completely decentralized blockchain network.
ZenCash is a community-oriented enterprise combining blockchain and related technologies in order to cultivate a social movement and create an environment for facilitating collaboration. Here we take a closer look at how ZenCash envisions blockchain as the catalyst for social change.
ZenCash is a split from the ZClassic blockchain, which itself was a fork of ZCash with some key modifications with respect to monetary policy and distribution. ZenCash likewise leverages and builds upon zero-knowledge cryptography (see below) in an effort to lay the foundations for a decentralized and truly anonymous post-Satoshi system over which communications, data, and value can be securely communicated and stored.
Zen is also partnered with research and development company IOHK, under the umbrella of which Cardano and Ethereum Classic are developed. IOHK was founded in 2015 by Charles Hoskinson (co-founder of Ethereum and BitShares, and senior advisor to ZenCash) as an organization dedicated to developing generalized solutions and industry standards for the broader landscape of distributed ledger technologies.
Zen’s set goals are to lower the barriers to entry and participation – technical and otherwise – in order to invite a more widely distributed and diverse form of decentralization, both geographical and political. A more democratic and farther reaching network would, over time, prove resilient and provide the necessary conditions for the system to grow, evolve, and sustain itself. In that respect, Zen is already one of the most distributed node architectures, accounting for about eleven thousand geographically distributed nodes, spread out mining pools and regional (representative and developer) teams around the globe.
Zero-knowledge Proofs (ZKP)
Zero-knowledge proofs are cryptographic constructions where a ‘prover’ can prove the validity of a statement about a secret, without revealing anything else about the secret itself. The concept was first proposed in the mid 80’s and has since become a cornerstone of modern cryptography.
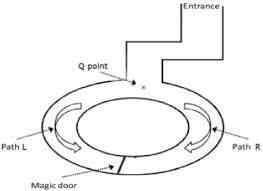
A common illustration of ZKP is the cave of Ali Baba, where Peggy (the prover, in place of the proverbial Alice and Bob) demonstrates to Victor (verifier) that she knows the magic word to open a door inside a cave by showing up on either of the two sides a number of times until Victor is convinced.
The basic intuition of zero-knowledge systems is that they take advantage of the extra knowledge conveyed by the proof, checking whether or not it satisfies the basic constraints of the protocol being followed, in order to convince the verifier and reach an agreement. On the blockchain, zero-knowledge proofs are a mechanism for validating transactions without revealing any further details about them.
ZCash > ZClassic > ZenCash
ZCash (ZEC) was the first blockchain implementation of zero-knowledge proofs which extended the Bitcoin protocol with enhanced privacy features. Unlike Bitcoin, however, the ZCash code base ensures a 20% founders’ fee for the first 4 years and a slow start to the number of blocks. In this way, scarcity is deliberately engineered into the network and founders are able to capture a large percentage of the total monetary supply.
ZClassic (ZCL) then emerged as a fork of ZCash that instead followed in the footsteps of Bitcoin by eliminating founders’ fees. Rewards go directly to miners in order to ensure wider decentralization, better security, and fair, market-driven distribution.
Eventually, this culminated with ZenCash, a blockchain split from ZClassic which additionally supplemented the network protocol with extended features and properties to form a more versatile, general purpose platform capable of sustaining itself. Notably, Zen makes use of secure nodes (which require more professional IT sysadmins to operate) to make blockchain traffic indistinguishable from regular HTTPS and employs a treasury system similar to the one implemented by Dash in order to provide continuous development and sustainability.
Presently, the Zen protocol is configured to allocate block rewards among three role-designated groups of network participants:
• Miners – 88%
• Treasury (ops and dev) – 8.5%
• Secure Node Operators – 3.5%
Functional Components
As a full-fledged privacy suite, Zen combines a set of existing technologies and consumer-friendly applications in an integrated functioning infrastructure secured by the largest network of economically incentivized nodes in the industry. While much of it is a work in progress and subject to change, the following components define the basic functionalities and ways in which transactions can be structured.
1) Regular T_ and Private Z_Transactions
Just like ZCash, there are two ways transactions can be broadcasted and recorded on the blockchain: traditional Bitcoin-like transactions (t_transactions) and shielded ones (z_transactions) for keeping private economic activity confidential (no decipherable information about addresses of sender, receiver and amounts transacted or value of balances involved is revealed in the process). A more detailed description of the protocol can be found here.
2) ZenTalk
One inconvenience of private transactions in ZCash is that they’re anonymous to the extent that nobody knows who is sending what to whom and one can’t tell the transacting parties on the network, which makes users often move communications off-chain. In Zen, information can be securely exchanged before and after shielded transfers and messages incorporated alongside private transactions so that users can securely conduct commerce on the platform without relying on any other channels and third parties.
3) ZenPub
Transactions can also be appended with documents hosted on secure nodes, allowing for an anonymous publishing layer and distributing access to publications to involved parties. Presently, this is done via IPFS (InterPlanetary File System) and GNUnet, with the prospect of Zen using DNS mapping of their own in the future.
4) ZenHide
ZenHide is the functionality which allows for completing transactions in adversarial environments by circumvention of censorship policies. The technique currently in place is domain fronting (on the application layer, similar to Signal and Telegram). Adjustments will most likely be made as policies change and new technologies emerge (both Google and Amazon disabled domain fronting in April 2018 in response to pressure from the Russian government over Telegram’s use of it).
5) Secure Node Infrastructure
Zen is the first platform to ever implement and enforce the basic security standards of TLS (Transport Layer Security) enabled communication which encrypts blockchain traffic between nodes and wallets making it indistinguishable from regular HTTPS web traffic. Secure nodes also work to solve cryptographic challenges associated with the computational validation of private transactions via a form of staking (with a stake of 42 ZEN required to run a secure node). Payouts to node operators are issued on a regular weekly basis.
The requirements for running a secure node are fairly affordable, requiring a dedicated domain name and a remote server with a minimum of 4GB RAM, 15 GB SSD and 64-bit Linux-based OS. Detailed instructions on how to set up a node can be found here and a calculator for estimating monthly returns is available here. Additionally, there’s a dedicated hosting service which offers to do all the work for less technical users at the cost of $9.99/month.
6) PoW Mining
Presently, ZEN (the platform’s native currency) is an equihash-based proof-of-work GPU mineable cryptocurrency in line with Zen’s egalitarian philosophy and efforts to maintain optimal decentralization of all subsystems (given that Equihash is fairly easy to mine and specifically designed to be ASIC resistant).
This will change, however, in light of Bitmain’s announced equihash ASIC miner and the overall ease with which custom hardware can be designed to outperform any general purpose hardware whenever there is an economic incentive to do so. In trying to counter the potentially centralizing threat of the mining industry, Zen intends to hard fork in June and change the hashing algorithm to Equihash-144-5 (which optimizes for higher memory mining) as a temporary fix for the time being. Much of the discussion on the matter takes place on ZenCash’s Github at https://github.com/ZencashOfficial/zen/issues/142.
Research and Development
As part of the IOHK, Zen is positioning itself as an incubator for sustainable and reusable solutions rather than a for-profit entity and in these endeavors it is collaborating with IOHK on two research projects: a provably secure programmatic treasury system as the foundation for a deployable digital democracy and a scalability study investigating a potential shift from linear (blockchain-sequential) to exponential scaling (similar to the DAG model employed by IOTA).
Treasury System, Voting Mechanisms, and DAOs
Zen has a placeholder DAO (Decentralized Autonomous Organization) for internal funding of the underlying blockchain development and maintenance which is similar to the incremental funding model used in Dash. The system allows for submitting improvement proposals and development projects which get pushed forward through overall community consensus and a fair voting mechanism (where, though zero-knowledge obfuscation, ballots are revealed only after the votes are counted at the end of the epoch). The proof-of-concept specifications of the treasury model are described in detail in a recently published paper and the implementation is compatible with all commonly used blockchain platforms today.
Scalability Studies
Zen is also partnered with IOHK scientists in exploring DAG (Directed Acyclic Graph) based approaches to scalability – in particular, the alignment in which incoming transactions validate previous ones, thereby empowering the network rather than any group in particular.
This is similar to IOTA’s approach (which is uniquely designed to suit the IoT landscape), but different in that it doesn’t entirely do away with blocks, but instead considers a DAG protocol where blocks can be solved in parallel rather than put on a single lane, which tends to congest the network as the frequency with which transactions arrive increases past a certain threshold.
Such efforts are significant as they aim to provide standard solutions for wider adoption and thereby accelerate interoperability and productive collaboration (as opposed to competitive rivalry).
Summary
Zen’s strategy in leveraging the technology’s societal impact is to build liquidity and trading volume through diverse partnerships and joint efforts (with OpenBazaar integration on the roadmap) while focusing on utility, user-friendliness and adequately meeting market demands. Zen has also launched a first of its kind (among cryptocurrencies) 24/7 user helpdesk with a ticketing system and a dedicated support team in its efforts to expand community and user base.





